Malicious GhostPoster browser extensions found with 840,000 installs
- January 17, 2026
- 10:23 AM
- 0

Another set of 17 malicious extensions linked to the GhostPoster campaign has been discovered in Chrome, Firefox, and Edge stores, where they accumulated a total of 840,000 installations.
The GhostPoster campaign was first reported by Koi Security researchers in December. They found 17 extensions that were hiding malicious JavaScript code in their logo images, which monitored browser activity and planted a backdoor.
The code fetches a heavily obfuscated payload from an external resource, which tracks the victim’s browsing activity, hijacks affiliate links on major e-commerce platforms, and injects invisible iframes for ad fraud and click fraud.
A new report from browser security platform LayerX indicates that the campaign is still ongoing despite being exposed, and the following 17 extensions are part of it:
- Google Translate in Right Click – 522,398 installs
- Translate Selected Text with Google – 159,645 installs
- Ads Block Ultimate – 48,078 installs
- Floating Player – PiP Mode – 40,824 installs
- Convert Everything – 17,171 installs
- Youtube Download – 11,458 installs
- One Key Translate – 10,785 installs
- AdBlocker – 10,155 installs
- Save Image to Pinterest on Right Click – 6,517 installs
- Instagram Downloader – 3,807 installs
- RSS Feed – 2,781 installs
- Cool Cursor – 2,254 installs
- Full Page Screenshot – 2,000 installs
- Amazon Price History – 1,197 installs
- Color Enhancer – 712 installs
- Translate Selected Text with Right Click – 283 installs
- Page Screenshot Clipper – 86 installs
According to the researchers, the campaign originated on Microsoft Edge and then expanded to Firefox and Chrome.
LayerX found that some of the above extensions have been present in browser add-on stores since 2020, indicating a successful long-term operation.

Source: LayerX
Although evasion and post-activation capabilities remain mostly the same as previously documented by Koi, LayerX has identified a more advanced variant in the ‘Instagram Downloader’ extension.
The difference consists of moving the malicious staging logic into the extension’s background script and using a bundled image file as a covert payload container rather than only an icon.
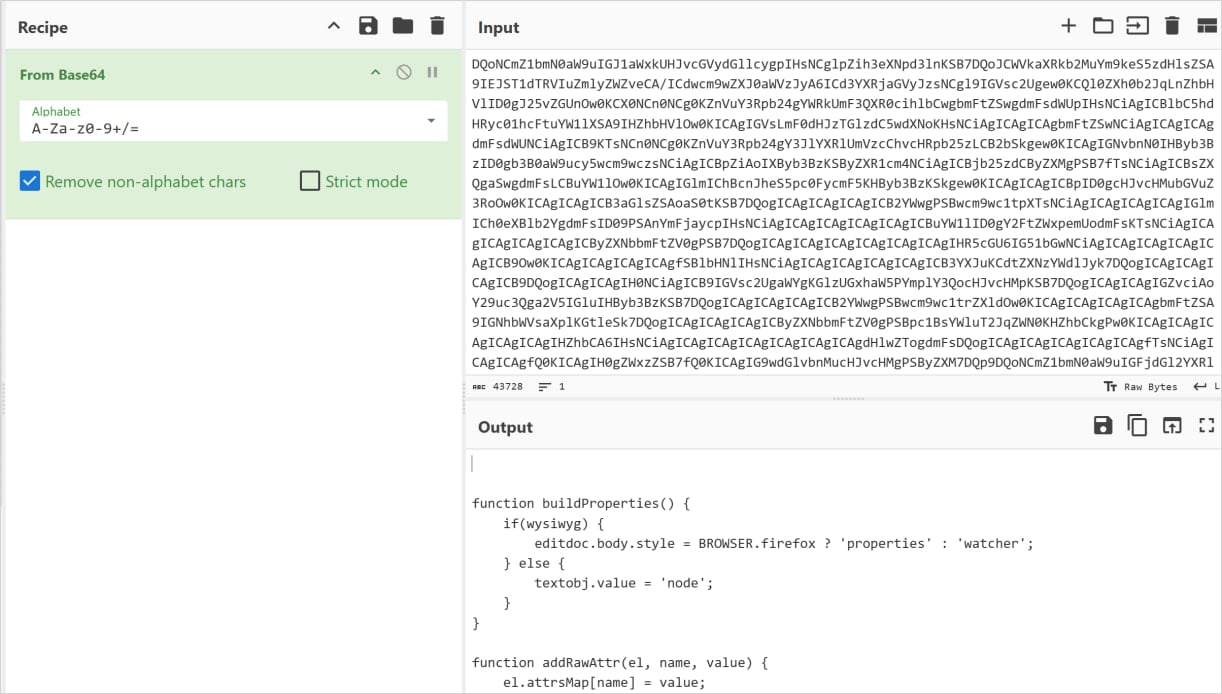
Source: LayerX
At runtime, the background script scans the image’s raw bytes for a specific delimiter (>>>>), extracts and stores the hidden data in local extension storage, then later Base64-decodes and executes it as JavaScript.
“This staged execution flow demonstrates a clear evolution toward longer dormancy, modularity, and resilience against both static and behavioral detection mechanisms,” comments LayerX about the newest GhostPoster variant.
The researchers said that the newly identified extensions are no longer present in Mozilla’s and Microsoft’s add-on stores. However, users who installed them in their browsers may still be at risk.
BleepingComputer has contacted Google about the extensions being present in the Chrome Web Store, and a spokesperson confirmed that all of them have been removed.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
Source: www.bleepingcomputer.com

