New PDFSider Windows malware deployed on Fortune 100 firm’s network
- January 19, 2026
- 04:00 PM
- 0

Ransomware attackers targeting a Fortune 100 company in the finance sector used a new malware strain, dubbed PDFSider, to deliver malicious payloads on Windows systems.
The attackers employed social engineering in their attempt to gain remote access by impersonating technical support workers and to trick company employees into installing Microsoft’s Quick Assist tool.
Researchers at cybersecurity company Resecurity found PDFSider during an incident response and describe it as a stealthy backdoor for long-term access, noting that it shows “characteristics commonly associated with APT tradecraft.”
Legit .EXE, malicious .DLL
A Resecurity spokesperson told BleepingComputer that PDFSider has been seen deployed in Qilin ransomware attacks. However, the company’s threat hunting team notes that the backdoor is already “actively used” by multiple ransomware actors to launch their payloads.
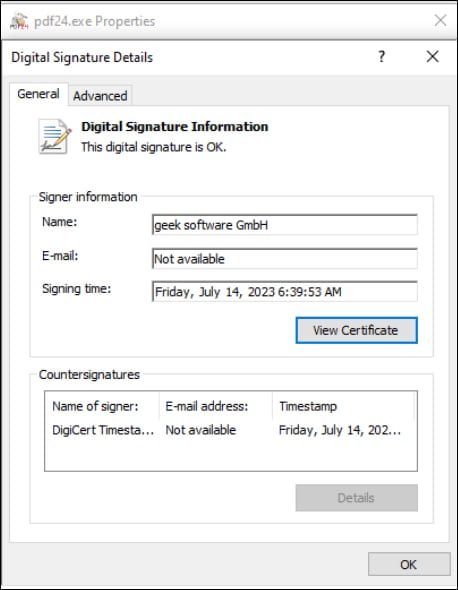
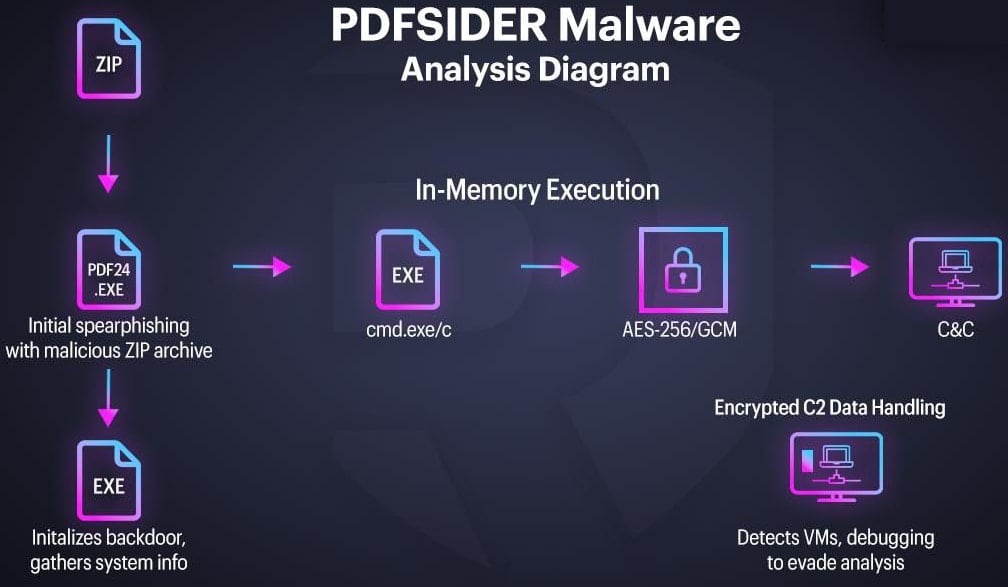
The PDFSider backdoor is delivered via spearphishing emails that carry a ZIP archive with a legitimate, digitally signed executable for the PDF24 Creator tool from Miron Geek Software GmbH. However, the package also includes a malicious version of a DLL (cryptbase.dll), which the application requires to function properly.
When the executable runs, it loads the attacker’s DLL file, a technique known as DLL side-loading, and provides code execution on the system.
Source: Resecurity
In other cases, the attacker attempts to trick email recipients into launching the malicious file by using decoy documents that appear to be tailored to the targets. In one example, they used a Chinese government entity as the author.
Once launched, the DLL runs with the rights of the executable that loaded it.
“The EXE file has a legitimate signature; however, the PDF24 software has vulnerabilities that attackers were able to exploit to load this malware and bypass EDR systems effectively,” Resecurity explains.
According to the researchers, finding vulnerable software that can be exploited is becoming easier for cybercriminals, due to the rise of AI-powered coding.
PDFSider loads straight into memory, leaving minimal disk artifacts, and uses anonymous pipes to launch commands via CMD.
Infected hosts are assigned a unique identifier, and system information is collected and exfiltrated to the attacker’s VPS server over DNS (port 53).
PDFSider protects its command-and-control (C2) exchange by using the Botan 3.0.0 cryptographic library and AES-256-GCM for encryption, decrypting incoming data in memory to minimize its footprint on the host.
Moreover, the data is authenticated using Authenticated Encryption with Associated Data (AEAD) in GCM mode.
“This type of cryptographic implementation is typical of remote shell malware used in targeted attacks, where maintaining the integrity and confidentiality of communications is critical,” Resecurity notes.
Source: Resecurity
The malware also features several anti-analysis mechanisms, such as RAM size checks and debugger detection, to exit early when signs of running in a sandbox are detected.
Based on its assessment, Resecurity says that PDFSider is closer to “espionage tradecraft than financially motivated malware” and is built as a stealthy backdoor that can maintain long-term covert access and provide flexible remote command execution and encrypted communication.
The 2026 CISO Budget Benchmark
It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
Source: www.bleepingcomputer.com

