SmarterMail auth bypass flaw now exploited to hijack admin accounts
- January 22, 2026
- 01:44 PM
- 0

Hackers began exploiting an authentication bypass vulnerability in SmarterTools’ SmarterMail email server and collaboration tool that allows resetting admin passwords.
An authentication bypass vulnerability in SmarterTools SmarterMail, which allows unauthenticated attackers to reset the system administrator password and obtain full privileges, is now actively exploited in the wild.
The issue resides in the force-reset-password API endpoint, which is intentionally exposed without authentication.
Researchers at cybersecurity company watchTowr reported the issue on January 8, and SmarterMail released a fix on January 15 without an identifier being assigned.
After the issue was addressed, the researchers found evidence that threat actors started to exploit it just two days later. This suggests that hackers reverse-engineered the patch and found a way to leverage the flaw.
SmarterMail is a self-hosted Windows email server and collaboration platform developed by SmarterTools that provides SMTP/IMAP/POP email, webmail, calendars, contacts, and basic groupware features.
It is typically used by managed service providers (MSPs), small and medium-sized businesses, and hosting providers offering email services. SmarterTools claims that its products have 15 million users in 120 countries.
The CVE-less flaw arises from the API endpoint ‘force-reset-password’ accepting attacker-controlled JSON input, including a ‘IsSysAdmin’ bool type property, which, if set to ‘true,’ forces the backend to execute the system administrator password reset logic.
However, the mechanism does not perform any security controls or verify the old password, despite the ‘OldPassword’ field being present in the request, watchTowr researchers found.
As a result, anyone who knows or guesses an admin username could set a new password and hijack the account.
The researchers note that the flaw affects only admin-level accounts, not regular users.
With admin-level access, attackers can run OS commands, thus getting full remote code execution on the host.
watchTowr researchers have created a proof-of-concept exploit that demonstrates SYSTEM-level shell access.
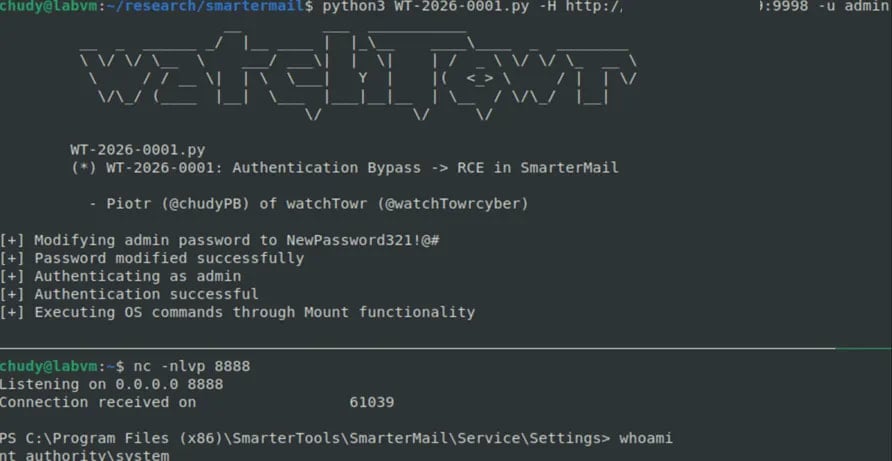
Source: watchTowr
The researchers learned that the vulnerability was being exploited in the wild from an anonymous user, who stated that somebody was resetting administrator passwords.
To back their claims, the tipster pointed watchTowr researchers to a forum post describing a similar situation.
Examining the shared logs revealed that these attacks targeted the ‘force-reset-password’ endpoint, supporting the conclusion that the issue is currently under active exploitation.
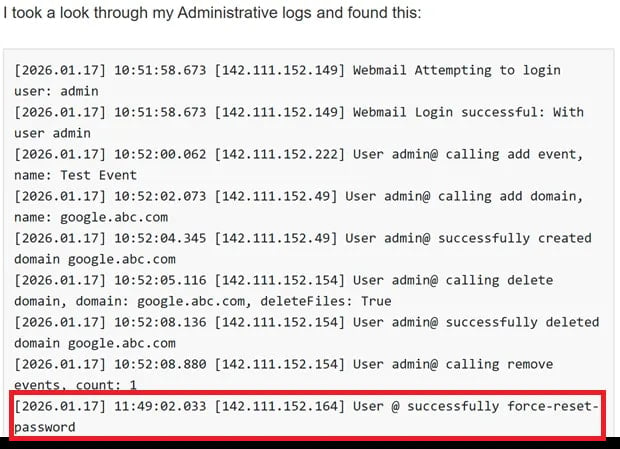
Source: watchTowr
Two weeks earlier, watchTowr discovered a critical pre-auth RCE flaw in SmarterMail, tracked as CVE-2025-52691, which led to the discovery of the latest issue.
Users of SmarterMail are recommended to upgrade to the latest version of the software, Build 9511, released on January 15, that addresses both issues.
The 2026 CISO Budget Benchmark
It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
Source: www.bleepingcomputer.com

